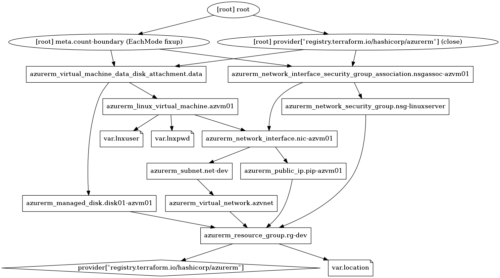
En premier, on déclare le provider :
provider "azurerm" {
features {}
}
Nos variables : la région Azure et les credentials pour la VM qui va être déployée
variable "location" {
type = string
default = "westeurope"
}
variable "lnxuser" {
type = string
default = "super"
}
variable "lnxpwd" {
type = string
default = "Azerty37!"
}
Toutes nos ressources vont être dans un même groupe de ressources :
resource "azurerm_resource_group" "rg-dev" {
name = "rg-dev"
location = var.location
tags = {
environment = "Development"
}
}
Nous aurons un vNet en 10.0.0.0/16 pour notre site Azure que l’on va redécouper et un subnet 10.0.1.0/24 pour notre VM de dev. Enfin, notre VM sera directement accessible avec une IP publique qu’il faut instancier séparément.
resource "azurerm_virtual_network" "azvnet" {
name = "vNet-${var.location}"
address_space = ["10.0.0.0/16"]
location = azurerm_resource_group.rg-dev.location
resource_group_name = azurerm_resource_group.rg-dev.name
}
resource "azurerm_subnet" "net-dev" {
name = "net-dev"
resource_group_name = azurerm_resource_group.rg-dev.name
virtual_network_name = azurerm_virtual_network.azvnet.name
address_prefixes = ["10.0.1.0/24"]
}
resource "azurerm_public_ip" "pip-azvm01" {
name = "pip-azvm01"
resource_group_name = azurerm_resource_group.rg-dev.name
location = azurerm_resource_group.rg-dev.location
allocation_method = "Dynamic"
tags = {
environment = "Development"
}
}
On peut désormais déployer notre VM avec la dernière image Ubuntu 20.04 LTS. Pour des questions de coûts, elle sera de type Standard_B1ls.
resource "azurerm_linux_virtual_machine" "azvm01" {
name = "azvm01"
resource_group_name = azurerm_resource_group.rg-dev.name
location = var.location
size = "Standard_B1ls"
admin_username = var.lnxuser
admin_password = var.lnxpwd
disable_password_authentication = false
network_interface_ids = [
azurerm_network_interface.nic-azvm01.id,
]
source_image_reference {
publisher = "Canonical"
offer = "0001-com-ubuntu-server-focal"
sku = "20_04-lts"
version = "latest"
}
os_disk {
storage_account_type = "Standard_LRS"
caching = "ReadWrite"
}
tags = {
environment = "Development"
}
}
resource "azurerm_network_interface" "nic-azvm01" {
name = "nic-azvm01"
resource_group_name = azurerm_resource_group.rg-dev.name
location = var.location
ip_configuration {
name = "internal"
subnet_id = azurerm_subnet.net-dev.id
private_ip_address_allocation = "Dynamic"
public_ip_address_id = azurerm_public_ip.pip-azvm01.id
}
tags = {
environment = "Development"
}
}
On créé ensuite un Security Group qui autorise le ping et les connexions SSH entrantes que l’on attache à l’interface réseau de cette VM :
resource "azurerm_network_security_group" "nsg-linuxserver" {
name = "nsg-linuxserver"
location = azurerm_resource_group.rg-dev.location
resource_group_name = azurerm_resource_group.rg-dev.name
security_rule {
access = "Allow"
direction = "Inbound"
name = "ssh"
priority = 100
protocol = "Tcp"
source_port_range = "*"
source_address_prefix = "*"
destination_port_range = "22"
destination_address_prefix = "*"
}
security_rule {
access = "Allow"
direction = "Inbound"
name = "ping"
priority = 110
protocol = "Icmp"
source_port_range = "*"
source_address_prefix = "*"
destination_port_range = "*"
destination_address_prefix = "*"
}
}
resource "azurerm_network_interface_security_group_association" "nsgassoc-azvm01" {
network_interface_id = azurerm_network_interface.nic-azvm01.id
network_security_group_id = azurerm_network_security_group.nsg-linuxserver.id
}
Enfin, on peut rattacher un disque de données persistant de type localy redondant storage :
resource "azurerm_managed_disk" "disk01-azvm01" {
name = "disk01-azvm01"
location = azurerm_resource_group.rg-dev.location
create_option = "Empty"
disk_size_gb = 10
resource_group_name = azurerm_resource_group.rg-dev.name
storage_account_type = "Standard_LRS"
tags = {
environment = "Development"
}
}
resource "azurerm_virtual_machine_data_disk_attachment" "data" {
virtual_machine_id = azurerm_linux_virtual_machine.azvm01.id
managed_disk_id = azurerm_managed_disk.disk01-azvm01.id
lun = 0
caching = "None"
}
Il n’y a plus qu’à lancer le workflow Terraform :
az login terraform init terraform plan terraform apply